
Using Windows Server NPS for AAA in Unimus
In this guide, we show you how Microsoft's Network Policy Server, or NPS for short, can be configured to act as a RADIUS server for AAA in Unimus. By using NPS, you can use your domain (AD) credentials to login to Unimus.
In this guide, we would like to show how Microsoft's Network Policy Server, or NPS for short, can be configured to act as a RADIUS server to handle AAA for Unimus. By using NPS, you can use your Windows domain (Active Directory) credentials to login to Unimus.
In this guide we assume you are already running Windows Server, Active Directory, and have installed the NPS server. If you don't have an NPS server installed yet, you can do so by navigating to Add roles and features > Role-based or feature-based installation > Select your machine > Network Policy and Access Services. Follow the wizard and confirm the dependencies it will list.
Preparing for NPS - Windows Server 2019 users
If you are running Windows Server 2019 you will need to look at one current bug, which directly touches NPS, and causes the traffic to be dropped at the firewall level despite the default port rules set up by NPS. You can fix the issue by opening the Command Prompt and running this command:
sc sidtype IAS unrestrictedPlease restart the server after you make the change.
You can read more about this issue here or here.
Preparing for NPS - Users and Groups in Active Directory
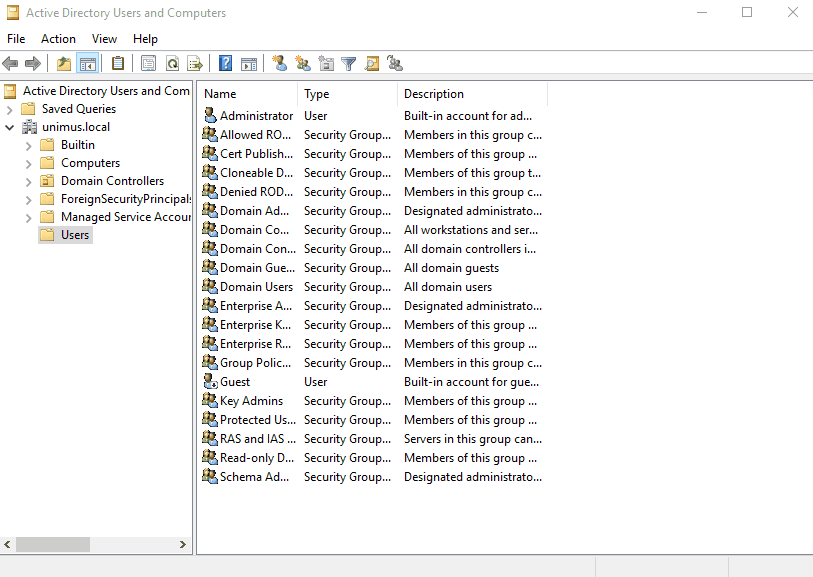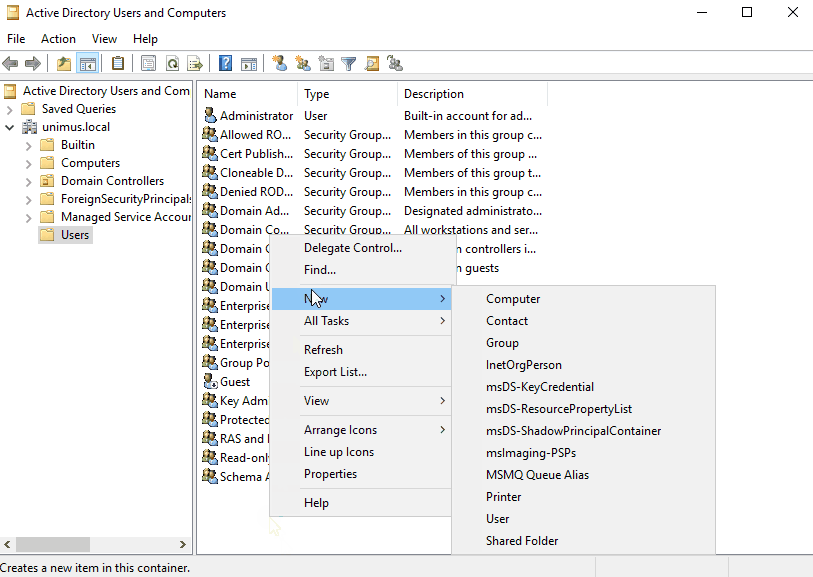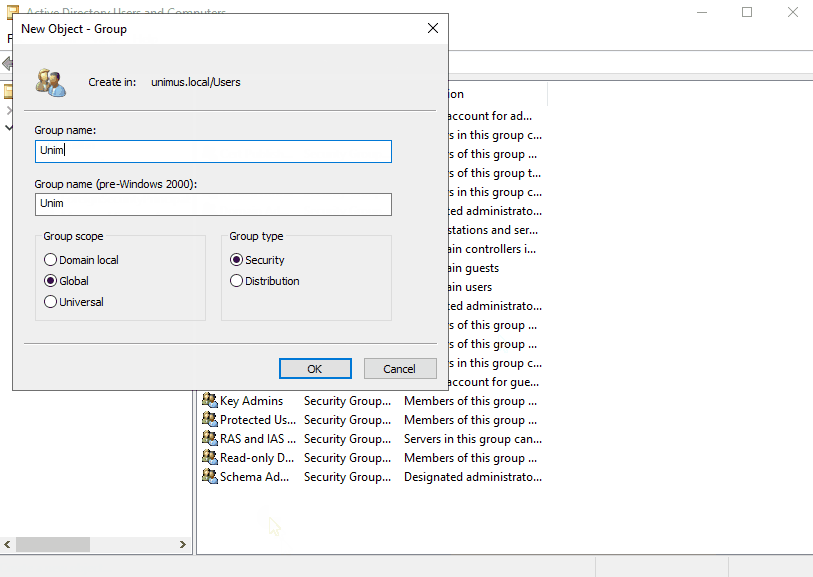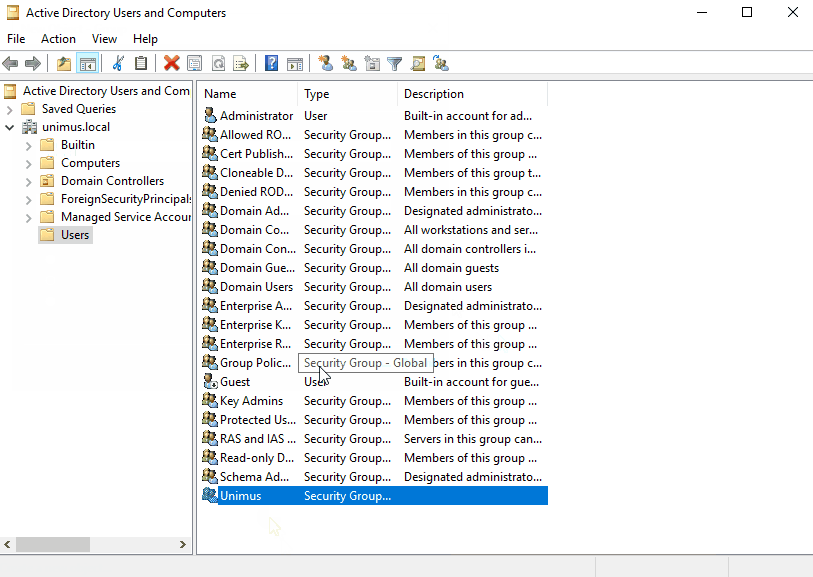
To start, create a user group. This user group will be used as a condition for a network policy in NPS to authenticate users later:
Next, create a user. This will be a user we want to grant access to Unimus:
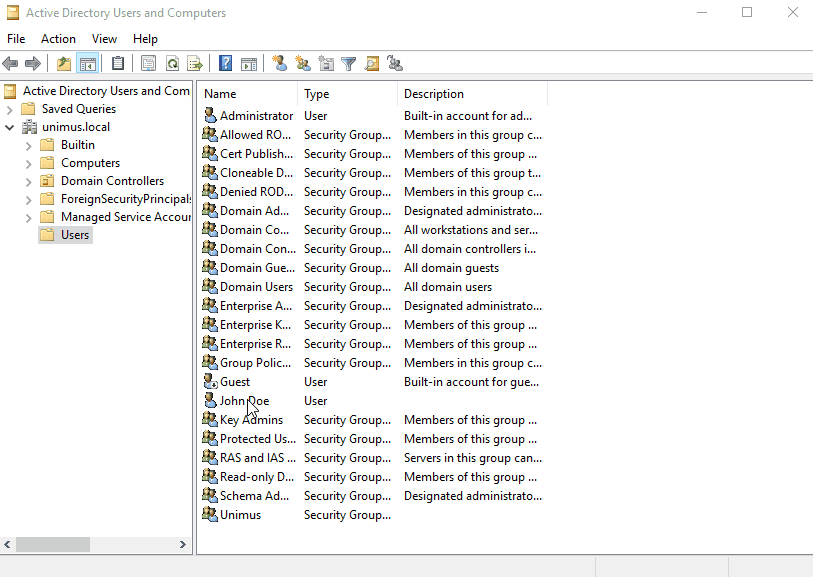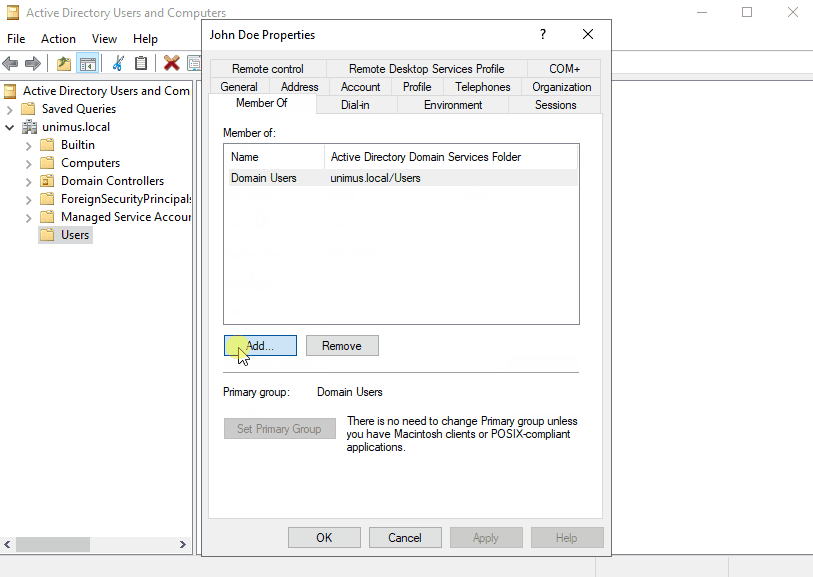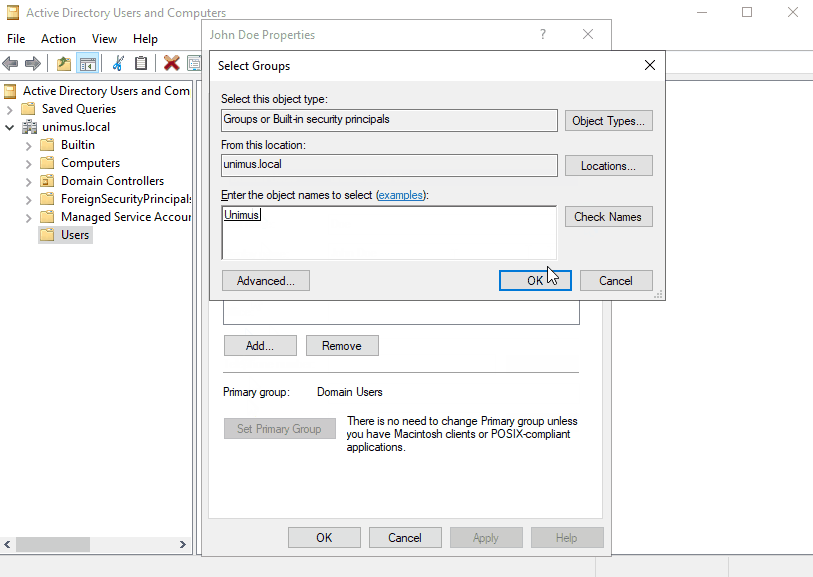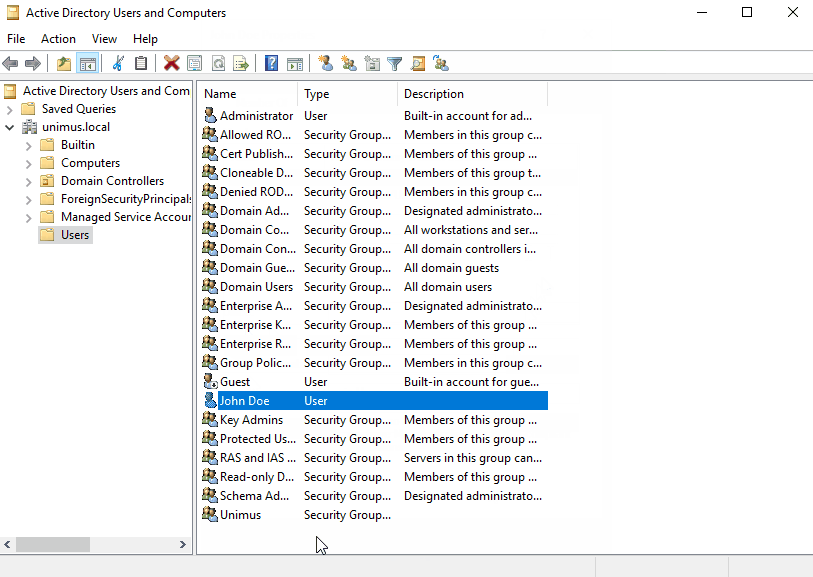
Then add the user(s) to the group you created earlier:
Preparing for NPS - Authentication methods
Before we start configuring NPS, we need to decide on the auth protocol we will use. Unimus currently supports two authentication methods, PAP and CHAP.
PAP (Password Authentication Protocol)
PAP is, by all means, an insecure protocol. When using PAP, the password is sent hashed using the shared secret between the RADIUS client (Unimus) and RADIUS server (NPS). This exposes the passwords to a risk, since anyone with the secret could reverse the password hashing and access passwords in plaintext.
Usually, we don't recommend using PAP. However, PAP has an advantage when compared to CHAP - the password on each end can be stored encrypted using any method. Since it can be encrypted in storage, the password is much more immune to leakage when then password storage is compromised.
In short, PAP encrypts passwords in storage, but transfers them as a cleartext hash over the network.
CHAP (Challenge-Handshake Authentication Protocol)
CHAP is a more secure method, which does not transfer passwords via the network at all. Instead, when a link is established between the RADIUS client (Unimus) and the RADIUS server (NPS), the server responds with a challenge (a salt - a random string). The client uses hashing for the password and the challenge and sends the hash via network to the server. This is then used for authentication on that end.
One disadvantage of CHAP is that both the password(s) must be stored in an unencrypted or reversibly encrypted format. This exposes password storage to a potential risk if the database (AD) is compromised. Healthy Active Directory security practices are recommended.
In short, CHAP transfers passwords over the network securely, however passwords must be stored in cleartext (or using reversible encryption) in storage.
What to do if you wish to use CHAP
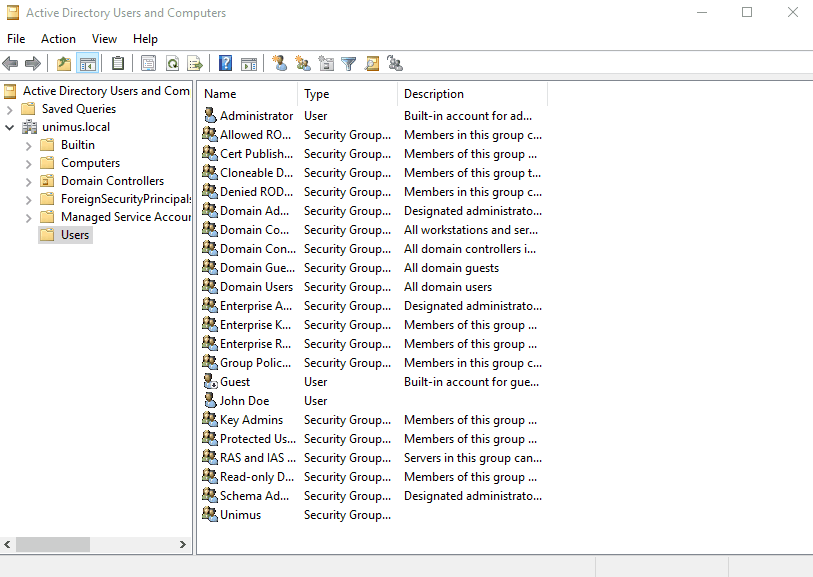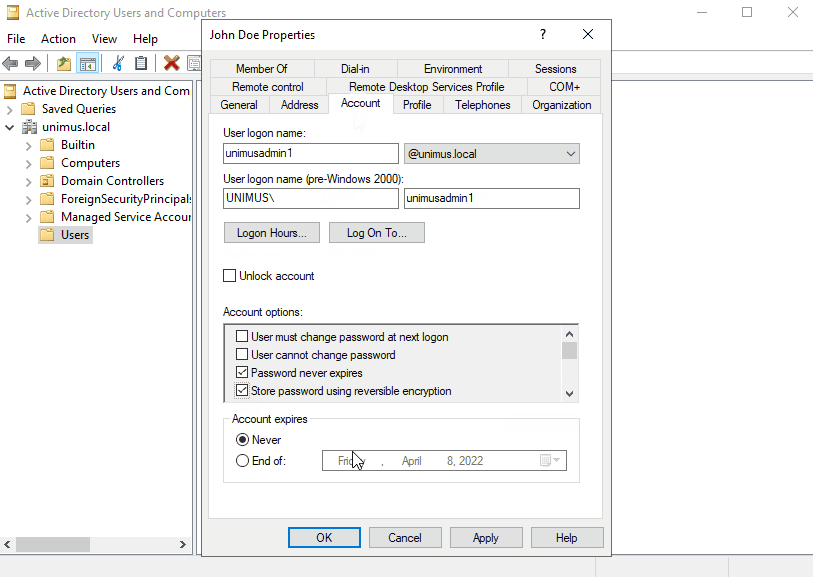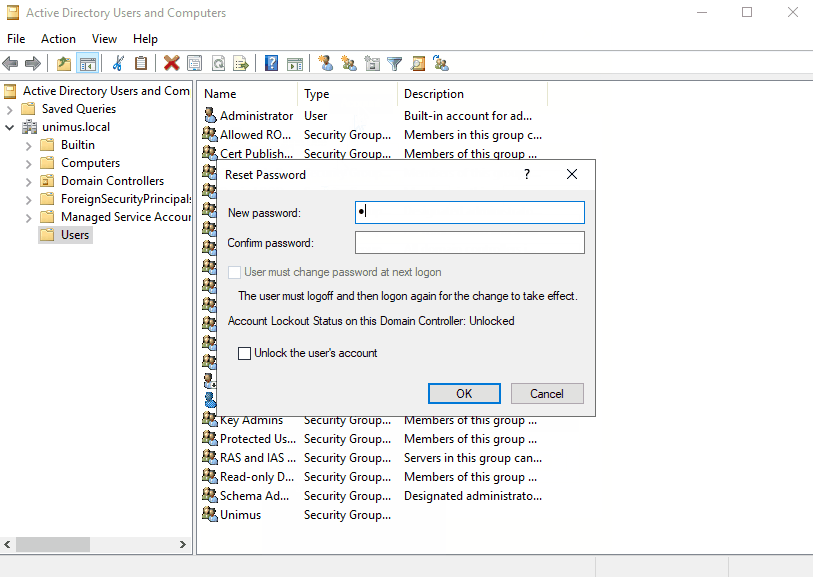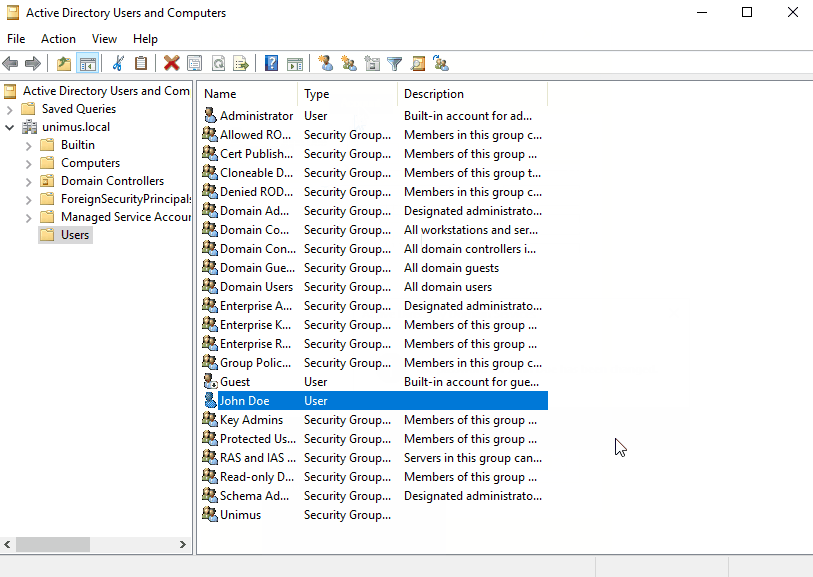
If you choose to use CHAP, then before proceeding we need to prepare accounts to be usable with CHAP. As in the section above, we will be making changes to Active Directory - User and Groups. You will need to enable reversible encryption for the user's password and reset the password afterwards:
NPS Configuration
Register the NPS server in Active Directory
To use NPS, it needs to be registered as an Active Directory service .To do so, right-click the NPS (Local) entry in the top-left corner of the NPS window and click on Register server in Active Directory.
Add Unimus as a RADIUS client
Next we need to create Unimus as an NPS RADIUS Client:
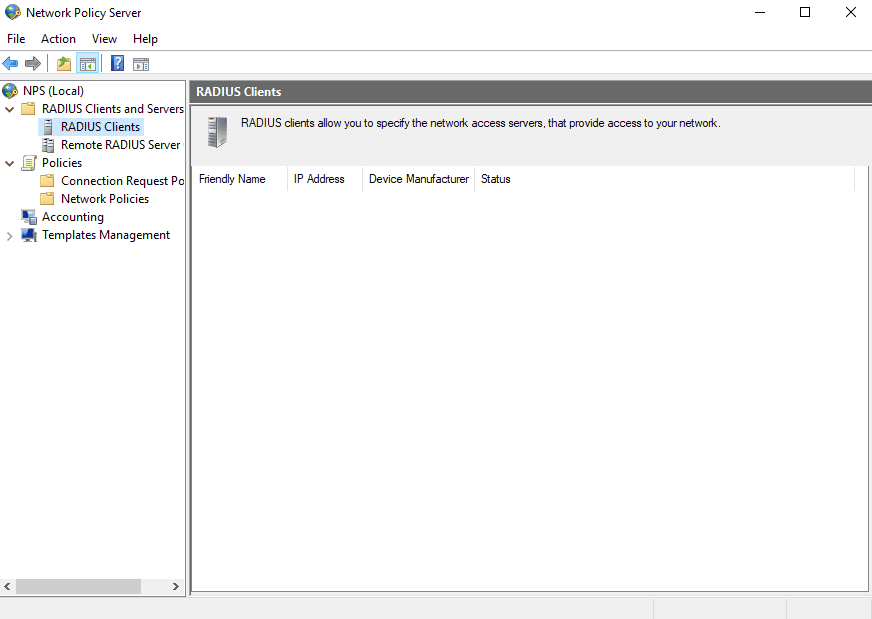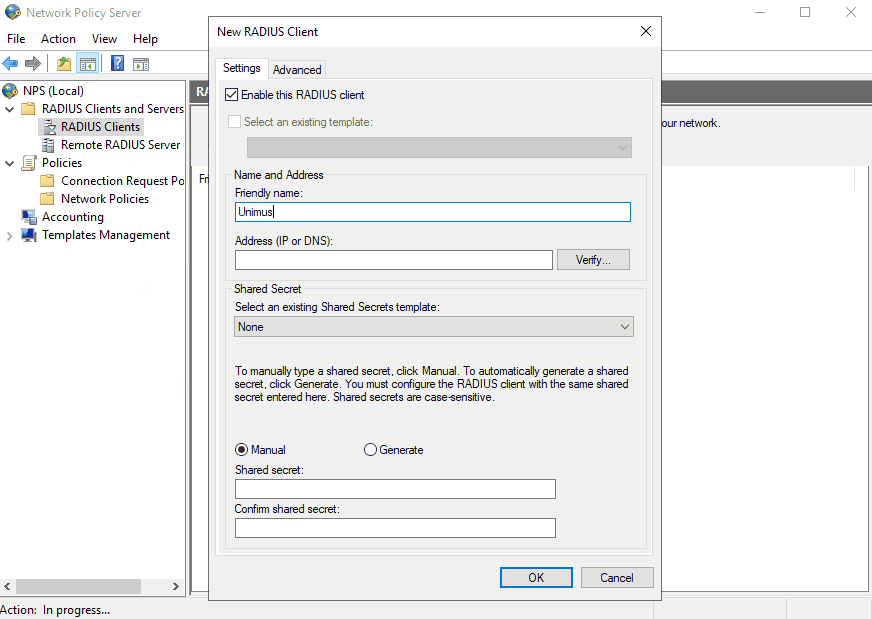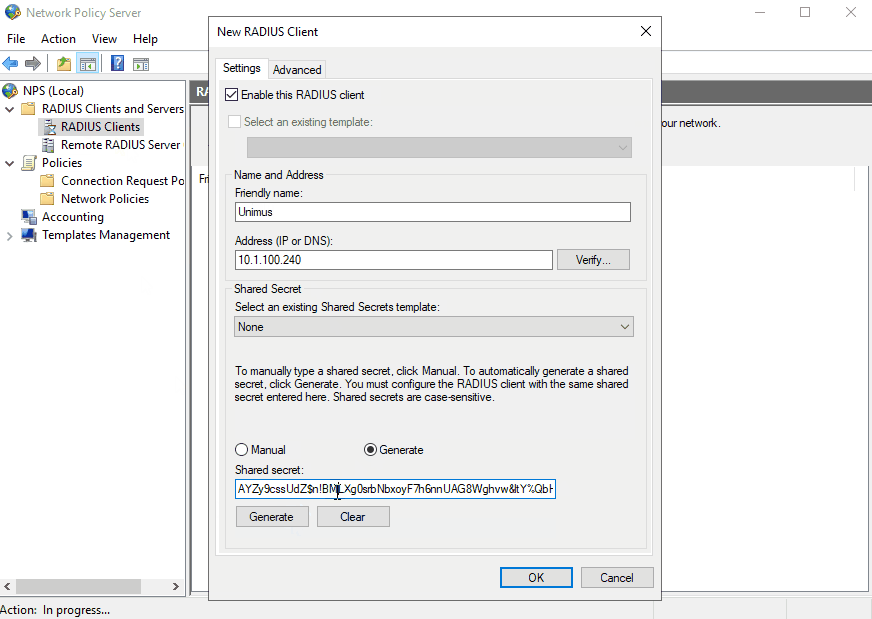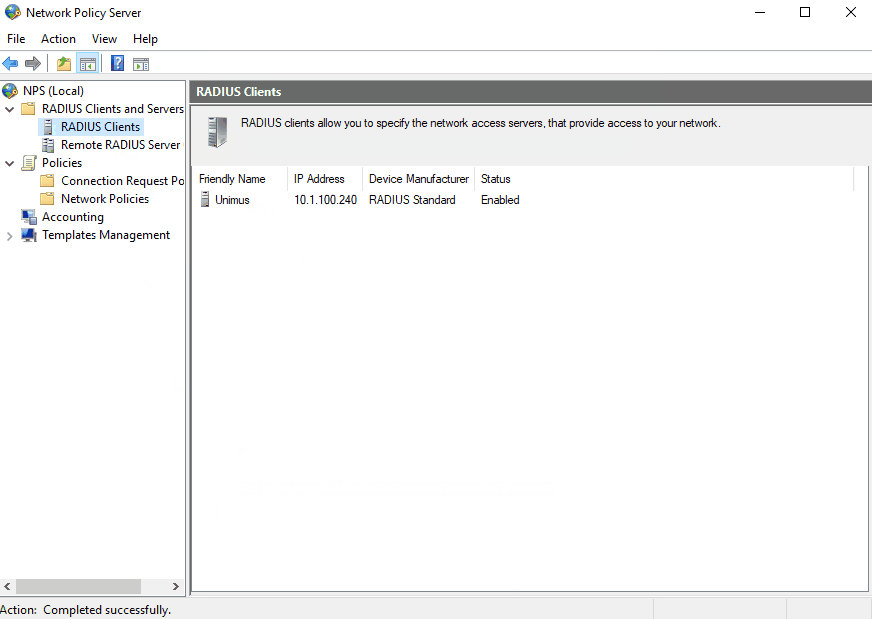
Don't forget to copy the generated secret and paste it somewhere. This secret will be used in the RADIUS configuration in Unimus.
Configure NPS Accounting
Configuring accounting on NPS is also extremely helpful:
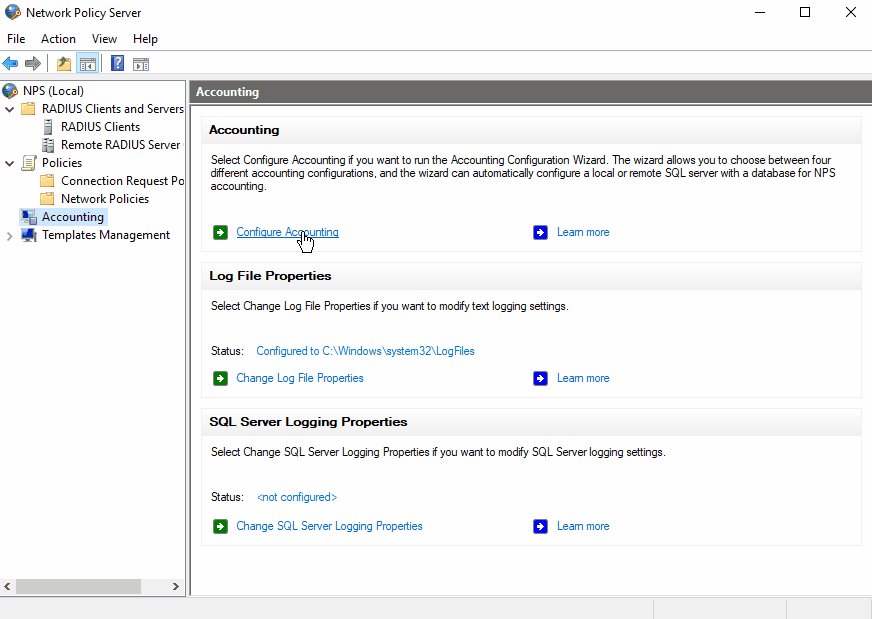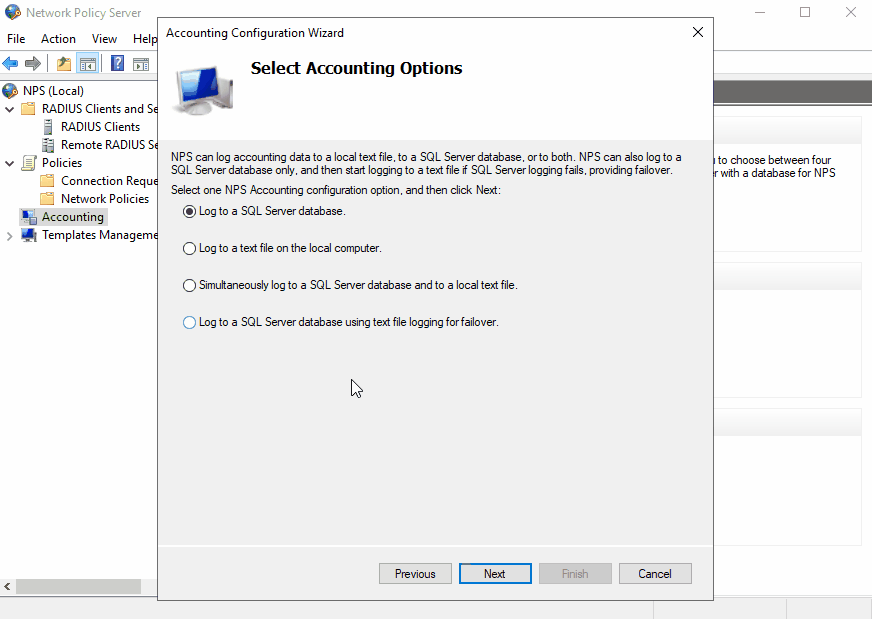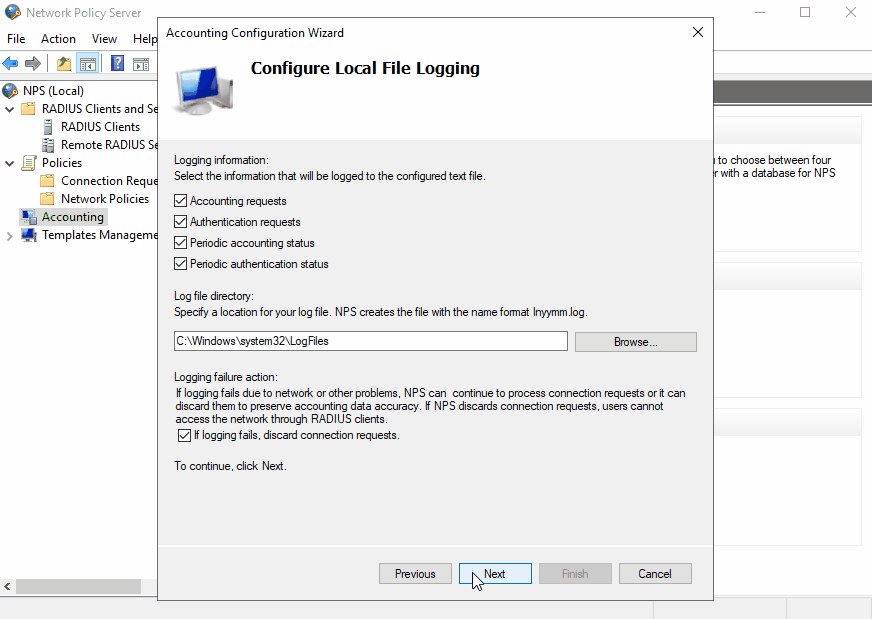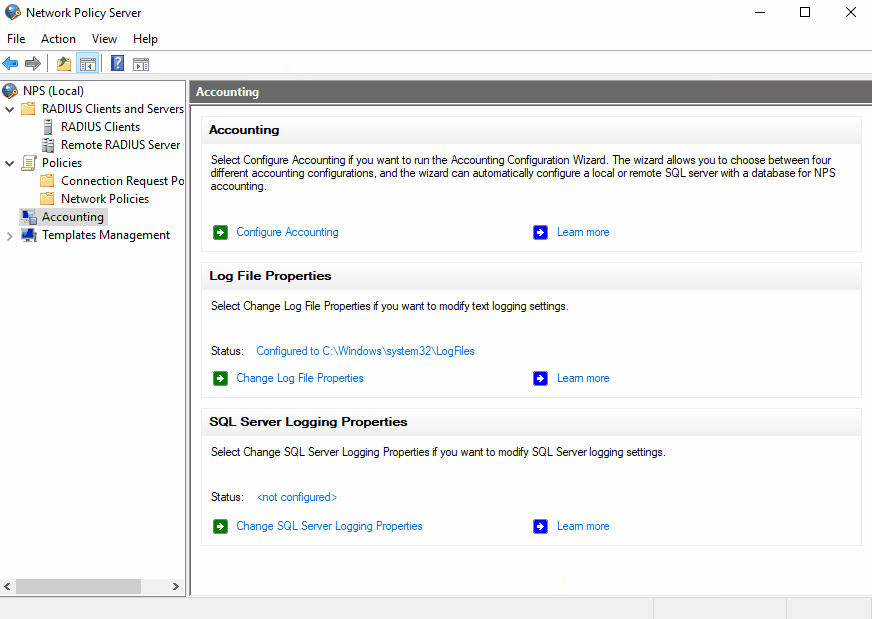
You can have NPS log into a database or a text file. If you prefer the database, you can connect it with your MSSQL database. Otherwise, logging to a file is the easier choice. You can also choose which type of records you want to log.
Create Network Policy for Unimus
To use Unimus with NPS, we need to create a policy:
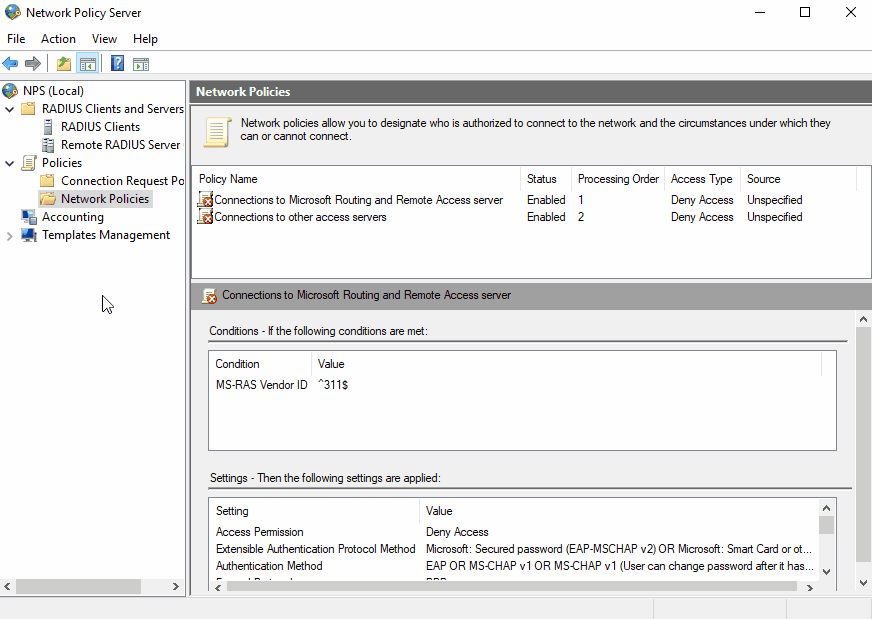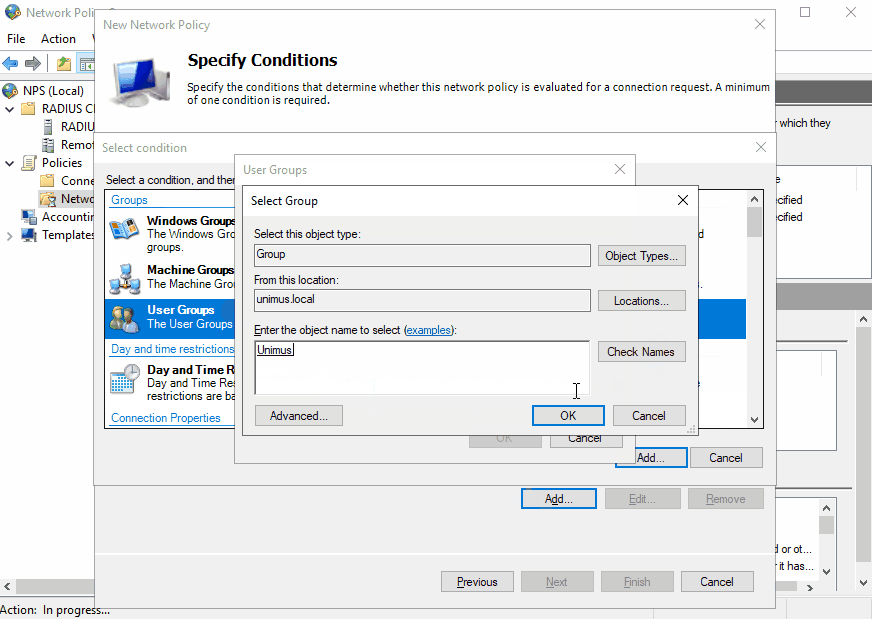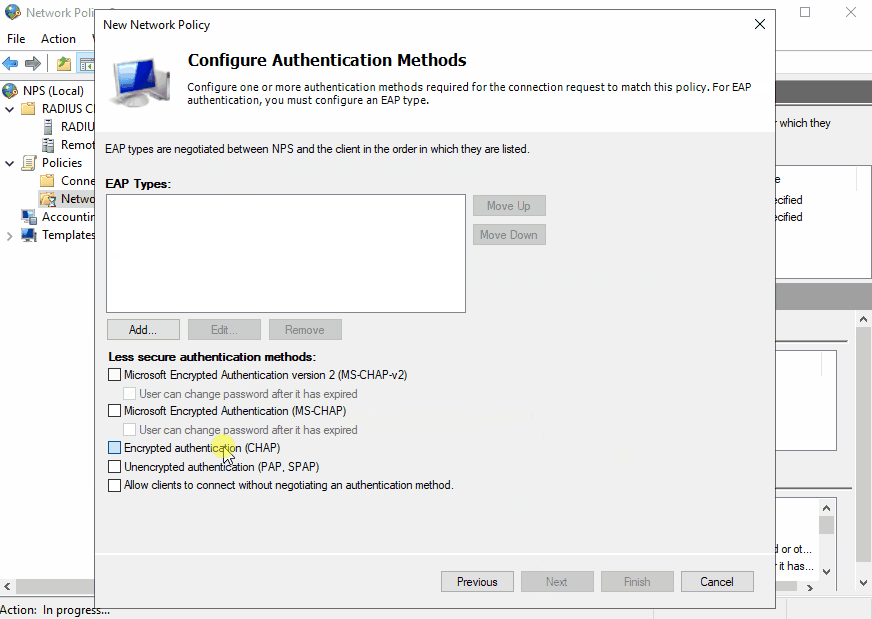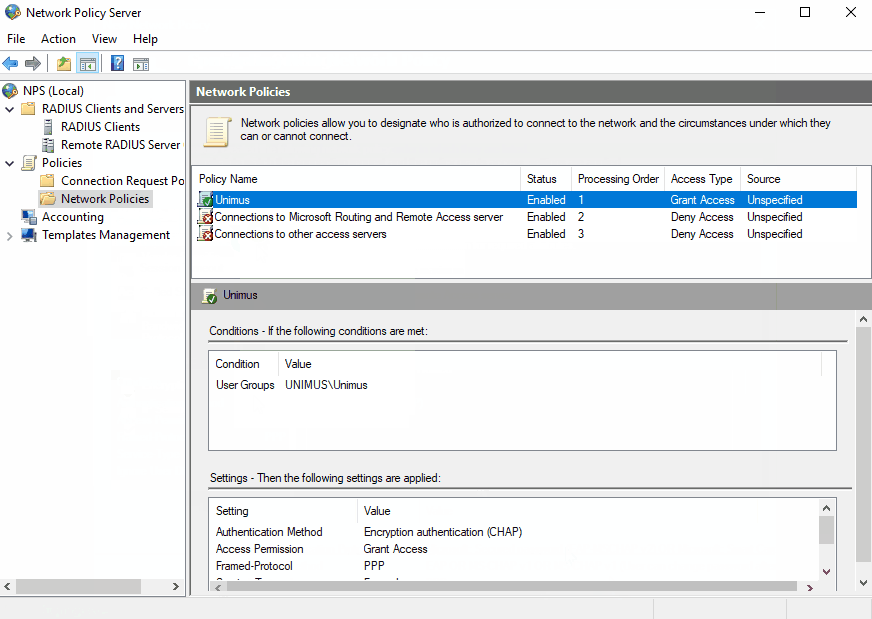
Let's run down through some of the sections when setting up a Network Policy:
Conditions - in this guide, we are using the membership in a user group as a condition for granting access. However, it is up to you if you require or wish to create more conditions or use different conditions to authenticate accounts.
Access Permission - unless you are setting up some specific network policies, we recommend creating a single network policy with Grant access permission.
Authentication Methods - here, we want to disable MS-CHAP v1 and v2 methods, which are not currently supported, and choose the PAP or CHAP method. Refer to the section above to decide which method is ideal or preferred for your use case.
Settings - this section defines settings which can be used upon access being granted. There is no requirement for Unimus to be defined here.
This is all that is needed to configure the NPS server to authenticate logins from Unimus. No extra configuration should be required and NPS should be ready at this point.
Unimus configuration - Configuring RADIUS
You can configure RADIUS in User management > Radius configuration:
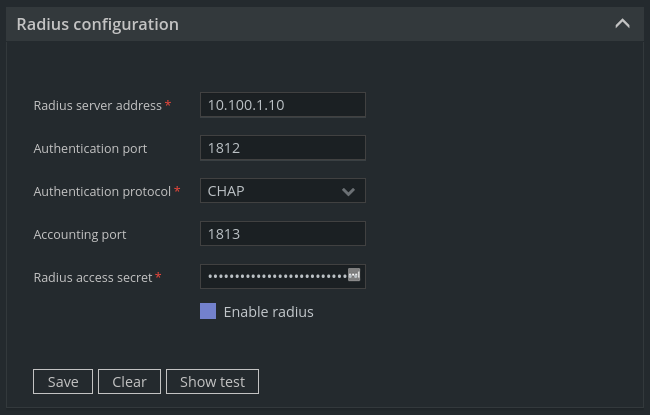
Where:
Radius server address - the address of the Windows Server machine running the NPS server.
Authentication port - the default port, unless changed, is 1812.
Authentication protocol - choose one you chose when creating the Network Policy in NPS.
Accounting port - the default port, unless changed, is 1813.
Radius access secret - the secret you generated when adding Unimus as the RADIUS client in the NPS.
You can also test if your configuration works by clicking Show test. You don't need to have a user account added to Unimus to test this. This test should pass if you follow this guide. If it doesn't, we have some troubleshooting steps for you at the end of this guide.
Unimus configuration - Adding RADIUS accounts to Unimus
Unimus currently requires every external user account to have a matching account in Unimus. You can create a user in User management > Users:
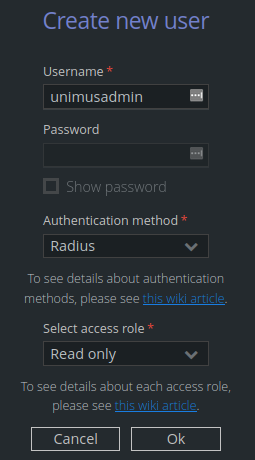
Where:
Username - the matching username as the external account in Active Directory.
Authentication method - Radius.
Select access role - select which role the user will represent.
At this point, users should be able to log into Unimus using RADIUS and their external account credentials.
Troubleshooting
In our experience, the most useful information when troubleshooting is directly on the Windows Server. Whether checking the Event Viewer or the NPS accounting log. Here's how.
Event Viewer
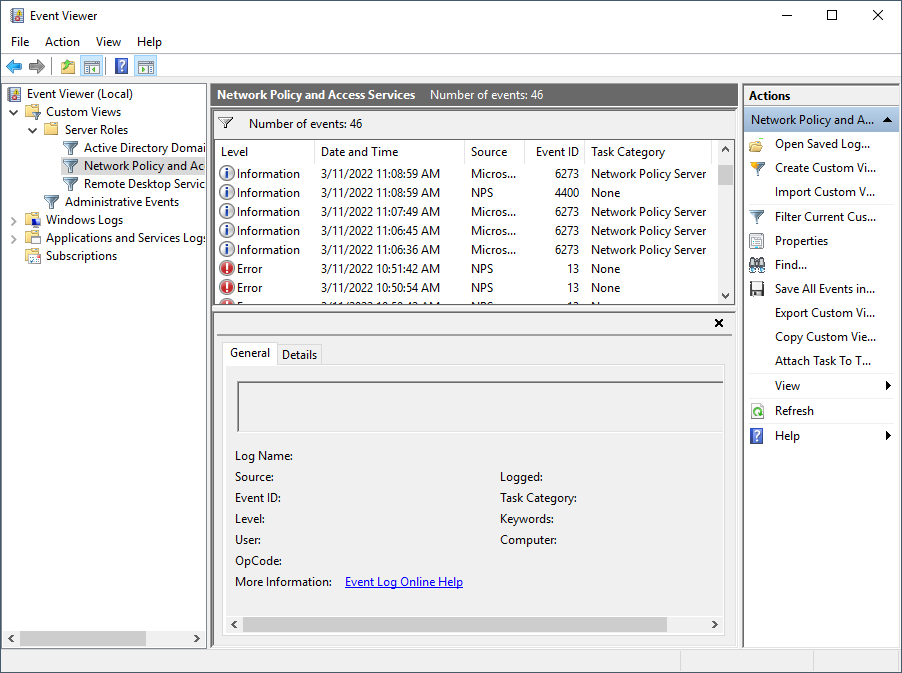
The Event Viewer provides a lot of clarity for possible events and errors. Every entry includes a message with a clear description of the problem and an Event ID, which can be used to search for possible solutions to Windows generic issues. Here are some examples of messages you may encounter:
| Log Level | Event ID | Message |
|---|---|---|
| Info | 6273 | Network Policy Server denied access to a user. |
| Info | 6272 | Network Policy Server granted access to a user. |
| Error | 13 | A RADIUS message was received from the invalid RADIUS client IP address 10.1.100.240. |
Fortunately, these messages are specific, and in the Details tab you can see even more details, including NPS's internal error interpretation. For example, this way you can see more details on events when users weren't granted access, like in the case of the first one above. The fields you are interested in are ReasonCode and Reason, and you can see information like this:
ReasonCode: 19
Reason: The user could not be authenticated using Challenge Handshake Authentication Protocol (CHAP). A reversibly encrypted password does not exist for this user account. To ensure that reversibly encrypted passwords are enabled, check either the domain password policy or the password settings on the user account.
This error for example, tells us the user's password is not stored in a reversibly encrypted format, which we can then check in the user's account. If the user already has the support checked, it is very likely the password wasn't reset after the change.
NPS Accounting log
While most of the information about a potential problem can be gathered and interpreted by the Even Viewer in a better human-readable form, the most important information is also included in the accounting log:
<Event>
<Timestamp data_type="4">03/11/2022 11:06:45.206</Timestamp>
<Computer-Name data_type="1">WIN-P3URXOXOR1T</Computer-Name>
<Event-Source data_type="1">IAS</Event-Source>
<Class data_type="1">311 1 10.100.1.111 03/03/2022 16:57:07 31</Class>
<Authentication-Type data_type="0">2</Authentication-Type>
<Fully-Qualifed-User-Name data_type="1">UNIMUS\unimusadmin</Fully-Qualifed-User-Name>
<Client-IP-Address data_type="3">10.9.21.123</Client-IP-Address>
<Client-Vendor data_type="0">0</Client-Vendor>
<Client-Friendly-Name data_type="1">Unimus</Client-Friendly-Name>
<Proxy-Policy-Name data_type="1">Use Windows authentication for all users</Proxy-Policy-Name>
<Provider-Type data_type="0">1</Provider-Type>
<SAM-Account-Name data_type="1">UNIMUS\unimusadmin</SAM-Account-Name>
<Packet-Type data_type="0">3</Packet-Type>
<Reason-Code data_type="0">19</Reason-Code>
</Event>
Final words
Hopefully this article can guide you through connecting Unimus with NPS. If you have any questions, or you run into any issues, please feel free to post in the Support section of our forums, or contact us through our usual support channels.
